卫报:‘意外的英雄’中止了勒索攻击并警告:这不是结束 [英国媒体]
“意外的英雄’通过注册隐藏在恶意软件中的一个乱码域名,中止了蔓延全球、前所未有的勒索攻击,并警告称攻击可能会重新启动。
'Accidental hero' halts ransomware attack and warns: this is not over
‘意外的英雄’中止了勒索攻击并警告:这不是结束
Expert who stopped spread of attack by activating software’s ‘kill switch’ says criminals will ‘change the code and start again’
专家通过激活软件的‘杀死开关’阻止了攻击的蔓延,称罪犯将‘改变代码重新开始’
The “accidental hero” who halted the global spread of an unprecedented ransomware attack by registering a garbled domain name hidden in the malware has warned the attack could be rebooted.
“意外的英雄’通过注册隐藏在恶意软件中的一个乱码域名,中止了蔓延全球、前所未有的勒索攻击,并警告称攻击可能会重新启动。
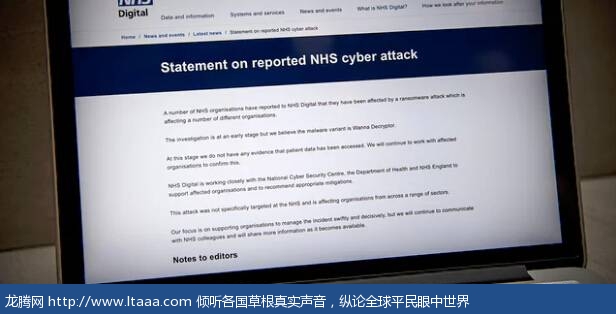
The ransomware used in Friday’s attack wreaked havoc on organisations including FedEx and Telefónica, as well as the UK’s National Health Service (NHS), where operations were cancelled, X-rays, test results and patient records became unavailable and phones did not work.
星期五的勒索攻击肆虐了包括FedEx和Telefónica在内的众多组织,以及英国国民健康服务(NHS),手术被取消,X光,检测结果以及病历不可使用,手机无法工作。
But the spread of the attack was brought to a sudden halt when one UK cybersecurity researcher tweeting as @malwaretechblog, with the help of Darien Huss from security firm Proofpoint, found and inadvertently activated a “kill switch” in the malicious software.
但是当一个英国网络安全研究院以@malwaretechblog发表推文,在来自安全公司Proofpoint的Darien Huss的帮助下,发现并无意中激活了恶意软件中的“杀死开关”后,攻击的蔓延突然中止了。
The researcher, who identified himself only as MalwareTech, is a 22-year-old from south-west England who lives with his parents and works for Kryptos logic, an LA-based threat intelligence company.
这个自称是MalwareTech的研究员,22岁,来自西南英格兰,和他的父母住在一起,就职于Kryptos logic,一个位于洛杉矶的威胁情报公司。
“I was out having lunch with a friend and got back about 3pm and saw an influx of news articles about the NHS and various UK organisations being hit,” he told the Guardian. “I had a bit of a look into that and then I found a sample of the malware behind it, and saw that it was connecting out to a specific domain, which was not registered. So I picked it up not knowing what it did at the time.”
“我正和一个朋友吃午饭,下午三点回去后看到大量关于NHS和各个英国组织被攻击的新闻报道,”他告诉卫报。“我瞟了一眼,然后发现了它背后的恶意软件样本,并看到它正连结着一个特定的域名,这个域名没有被注册。所以我当时拿起它但不知它当时做了什么。”
The kill switch was hardcoded into the malware in case the creator wanted to stop it spreading. This involved a very long nonsensical domain name that the malware makes a request to – just as if it was looking up any website – and if the request comes back and shows that the domain is live, the kill switch takes effect and the malware stops spreading. The domain cost $10.69 and was immediately registering thousands of connections every second.
杀死开关是植入恶意软件的硬编码,以便制作者想要阻止它扩散。这牵涉到一个该恶意软件提出请求的非常冗长的乱码域名,就像是在寻找什么网站,并且如果请求有了反馈,就说明该域名是激活的,杀死开关就会生效,恶意软件停止传播。这个域名花了10.69美元,并立即被以每秒数千次的连接来注册。
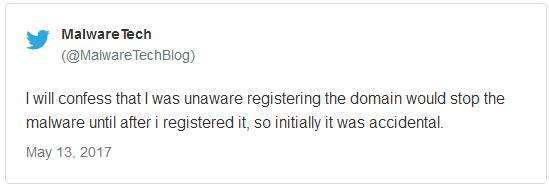
MalwareTech explained that he bought the domain because his company tracks botnets, and by registering these domains they can get an insight into how the botnet is spreading. “The intent was to just monitor the spread and see if we could do anything about it later on. But we actually stopped the spread just by registering the domain,” he said. But the following hours were an “emotional rollercoaster”.
MalwareTech解释说他购买这个域名因为他的公司要追踪僵尸网络,通过注册这些域名,他们可以了解到僵尸网络是如何传播的。“我们的目的只是监控传播,之后看看我们能否做些什么。但我们实际上通过注册域名阻止了传播,”他说。然而接下来的几个小时他的心情就像在坐过山车。
“Initially someone had reported the wrong way round that we had caused the infection by registering the domain, so I had a mini freakout until I realised it was actually the other way around and we had stopped it,” he said.
“最初有人还错误地说我们注册域名造成了感染,所以我有点崩溃,直到我意识到这实际上刚好相反,我们已经中止了它,”他说。
MalwareTech said he preferred to stay anonymous “because it just doesn’t make sense to give out my personal information, obviously we’re working against bad guys and they’re not going to be happy about this.”
MalwareTech说他宁愿保持匿名“因为把我的个人信息公布出来毫无道理,很明显我们在和坏人斗争,而他们不会乐见此事。”
He also said he planned to hold onto the URL, and he and colleagues were collecting the IPs and sending them off to law enforcement agencies so they can notify the infected victims, not all of whom are aware that they have been affected.
他还说他准备维持这个网址,他和同事们正收集IP并把它们送到执法部门,以便他们可以通知感染的受害者,他们中不是所有的人都已经意识到自己被影响了。
He warned people to patch their systems, adding: “This is not over. The attackers will realise how we stopped it, they’ll change the code and then they’ll start again. Enable windows update, update and then reboot.”
他警告人们要给他们的系统打补丁,并说:“这不是结束。攻击者会意识到我们是如何中止的,他们会改写代码并卷土重来。启动windows更新,更新后再重新启动。”
He said he got his first job out of school without any real qualifications, having skipped university to start up a tech blog and write software.
他说他离开学校找到了第一份工作,没有任何的资格证书而是跳过了大学创建了一个科技博客编写软件。
“It’s always been a hobby to me, I’m self-taught. I ended up getting a job out of my first botnet tracker, which the company I now work for saw and contacted me about, asking if I wanted a job. I’ve been working there a year and two months now.”
“这一直是我的一个爱好,我是自学成才的。最终我因为我的第一个僵尸网络跟踪器找到了一份工作,我现在就职的公司看到了然后联系我问我是否想要一份工作。我现在在那里工作一年零二个月了。”
But the dark knight of the dark web still lives at home with his parents, which he joked was “so stereotypical”. His mum, he said, was aware of what had happened and was excited, but his dad hadn’t been home yet. “I’m sure my mother will inform him,” he said.
但是这个暗网的黑暗骑士仍然和他的父母住在一起,他开玩笑说他们“非常刻板”。他说他的妈妈很关注发生了什么并且很激动,但他的爸爸现在不在家。“我我很确定我的母亲会通知他。”他说。
“It’s not going to be a lifestyle change, it’s just a five-minutes of fame sort of thing. It is quite crazy, I’ve not been able to check into my Twitter feed all day because it’s just been going too fast to read. Every time I refresh it it’s another 99 notifications.”
“这不会改变我的生活,这只是五分钟热度的事情。这很疯狂,我一整天都还没能够看看我的推特简讯因为它快得让人读不了。每次我刷新以后又有99+通知。”
Proofpoint’s Ryan Kalember said the British researcher gets “the accidental hero award of the day”. “They didn’t realise how much it probably slowed down the spread of this ransomware”.
Proofpoint的Ryan Kalember说这个英国研究院获得了“当日的意外英雄奖”。“他们没意识到它有多么能减缓这个勒索程序的扩散。”
The time that @malwaretechblog registered the domain was too late to help Europe and Asia, where many organisations were affected. But it gave people in the US more time to develop immunity to the attack by patching their systems before they were infected, said Kalember.
@malwaretechblog注册域名的时间太晚,没帮到欧洲和亚洲,已经有许多组织被影响。但它给了美国人更多时间去修补他们的系统,从而在被感染之前获得免疫力,Kalember说。
The kill switch won’t help anyone whose computer is already infected with the ransomware, and it’s possible that there are other variants of the malware with different kill switches that will continue to spread.
杀死开关不会帮到任何电脑已经被感染勒索程序的人,有可能还有其他的拥有不同杀死开关的变种恶意软件会继续传播。
The malware was made available online on 14 April through a dump by a group called Shadow Brokers, which claimed last year to have stolen a cache of “cyber weapons” from the National Security Agency (NSA).
这个恶意软件由一个叫Shadow Brokers的团体通过转储于4月14日在网上制造,这个团体声称去年从国安局(NSA)窃取了“网络武器”的缓存。
Ransomware is a type of malware that encrypts a user’s data, then demands payment in exchange for unlocking the data. This attack used a piece of malicious software called “WanaCrypt0r 2.0” or WannaCry, that exploits a vulnerability in Windows. Microsoft released a patch (a software update that fixes the problem) for the flaw in March, but computers that have not installed the security update remain vulnerable.
勒索软件是一种恶意软件,它加密用户数据,然后要求支付金钱作为交换来解锁数据。这种攻击使用一种利用Windows漏洞的,被称为“wanacrypt0r 2.0”或WannaCry的恶意软件。微软在3月为这个漏洞发布了补丁(一个软件更新,修复这个问题),但没有安装这个安全更新的计算机仍然很脆弱。
The ransomware demands users pay $300 worth of cryptocurrency Bitcoin to retrieve their files, though it warns that the “payment will be raised” after a certain amount of time. Translations of the ransom message in 28 languages are included. The malware spreads through email.
该勒索程序要求用户支付价值300美元的比特币恢复他们的文件,但他们警告说一段时间以后“价码会更高”。赎金信息被翻译成28种不同的语言。这个恶意软件通过电子邮件传播。
“This was eminently predictable in lots of ways,” said Kalember. “As soon as the Shadow Brokers dump came out everyone [in the security industry] realised that a lot of people wouldn’t be able to install a patch, especially if they used an operating system like Windows XP [which many NHS computers still use], for which there is no patch.”
Security researchers with Kaspersky Lab have recorded more than 45,000 attacks in 74 countries, including the UK, Russia, Ukraine, India, China, Italy, and Egypt. In Spain, major companies including telecommunications firm Telefónica were infected.
“这显然可以很多途径来预测,”Kalember说。“Shadow Brokers的转储一公开,安全行业的每个人就都意识到许多人将不能安装补丁,尤其是那些还在使用像Windows XP系统的人(许多NHS的电脑还在用),这就是没有补丁的原因。”卡巴斯基实验室的安全研究人员已经记录了超过45000次的攻击,在74个国家,包括英国,俄罗斯,乌克兰,印度,中国,意大利,埃及。在西班牙,大公司,包括电信公司Telefónicaó也被感染。
By Friday evening, the ransomware had spread to the United States and South America, though Europe and Russia remained the hardest hit, according to security researchers Malware Hunter Team. The Russian interior ministry says about 1,000 computers have been affected.
直到周五晚上之前,勒索程序已经传播到美国和南非,尽管据安全研究员Malware Hunter团队说欧洲和俄俄罗斯仍然是重灾区。俄罗斯内政部说大约1000台计算机已被感染。
版权声明
我们致力于传递世界各地老百姓最真实、最直接、最详尽的对中国的看法
【版权与免责声明】如发现内容存在版权问题,烦请提供相关信息发邮件,
我们将及时沟通与处理。本站内容除非来源注明五毛网,否则均为网友转载,涉及言论、版权与本站无关。
本文仅代表作者观点,不代表本站立场。
本文来自网络,如有侵权及时联系本网站。
图文文章RECOMMEND
热门文章HOT NEWS
-
1
最近,新冠肺炎疫情在日本有扩大的趋势,有专家呼吁日本应当举国行动起来,共...
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10
推荐文章HOT NEWS
-
1
最近,新冠肺炎疫情在日本有扩大的趋势,有专家呼吁日本应当举国行动起来,共...
- 2
- 3
- 4
- 5
- 6
- 7
- 8
- 9
- 10